Its Wednesday, currently, it may not be by the time this is done. In fact I’m almost certain that it will be after midnight. I would be shocked If I got all this done in 55 mins. Any way, what did you guys think and about The Shadow and Tom Waits. Super cool stuff right. Totally some thing that like Jack White would be into right lol. Anyway. Moving forward. The Deftones are pretty cool. Man, they sure have been a band for a while. Did you guys ever hear that White Pony album. Here, Ill hum a few bars from one of the tracks:
For some reason, that weirdly reminds me of my last relationship. Wow, was that too personal. Ultimately, I feel like I would be cheating my self if i didnt get slightly personal lol
Hey you guys see that new Slipknot? Damn that shit is hard.
Anyway… I guess we could get into some actual work and learning instead of being generic and attmepting to sk8 to prove we are cool
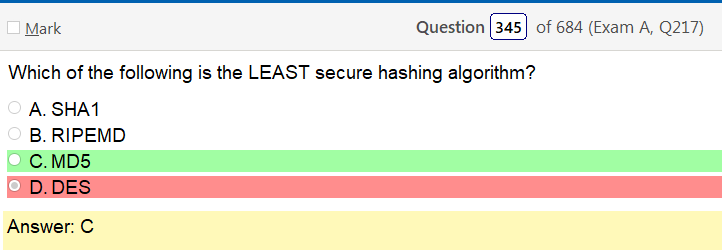
You know, this is uha, as previously noted these can be tricky so lets go through the definitions.
- SHA1 – typically rendered as a hexadecimal number, 40 digits long. It was designed by the United States National Security Agency, and is a U.S. Federal Information Processing Standard
- RIPEMD -a family of cryptographic hash functions developed in 1992 (the original RIPEMD) and 1996 (other variants). There are five functions in the family: RIPEMD, RIPEMD-128, RIPEMD-160, RIPEMD-256, and RIPEMD-320, of which RIPEMD-160 is the most common.
- The original RIPEMD, as well as RIPEMD-128, is not considered secure because 128-bit result is too small and also (for the original RIPEMD) because of design weaknesses. The 256- and 320-bit versions of RIPEMD provide the same level of security as RIPEMD-128 and RIPEMD-160, respectively; they are designed for applications where the security level is sufficient but longer hash result is necessary.
- While RIPEMD functions are less popular than SHA-1 and SHA-2, they are used, among others, in Bitcoin and other cryptocurrencies based on Bitcoin.
- MD5 – it has been found to suffer from extensive vulnerabilities
- DES -Data Encryption Standard is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits—criticized from the beginning—makes it too insecure for most current applications, it has been highly influential in the advancement of modern cryptography
Lots of options but per wikipedia MD5 is terrible.
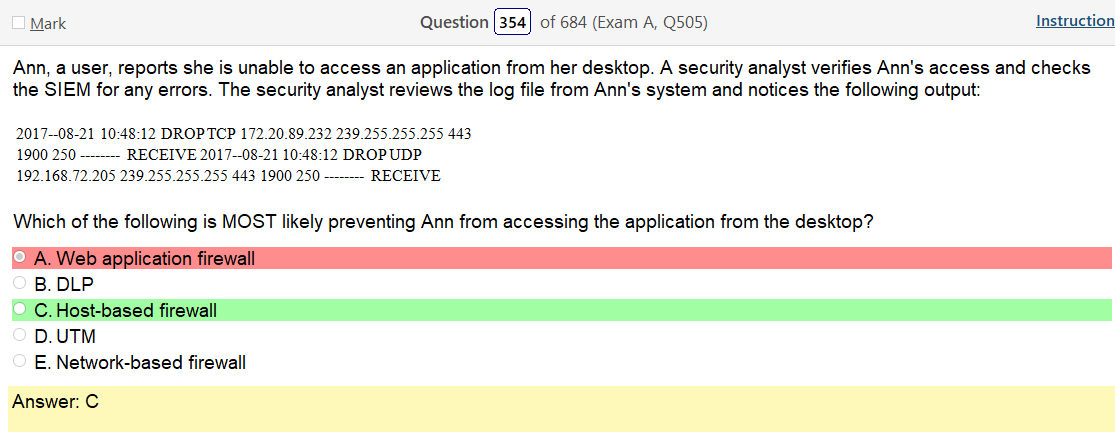
I can’t figure this one out are they saying the traffic is dropping at the 192.168 address? There are some things going on here that I’m not clear on. Honestly I would have to run a tracert to figure this out. The internet isnt going to be helpful and I have no idea what the hell kind of information that is.
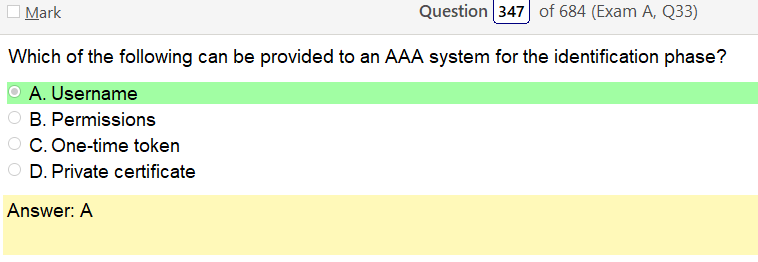
I got this right but it was kind of an obvious guess but I have no idea what an AAA system and I wanted to figure out what that is refers to Authentication, Authorization and Accounting. It is used to refer to a family of protocols that mediate network access. Two network protocols providing this functionality are particularly popular: the RADIUS protocol, and its newer Diameter counterpart.
Well, I guess I didnt really need to know that but its good to find out those sorts of things I suppose?
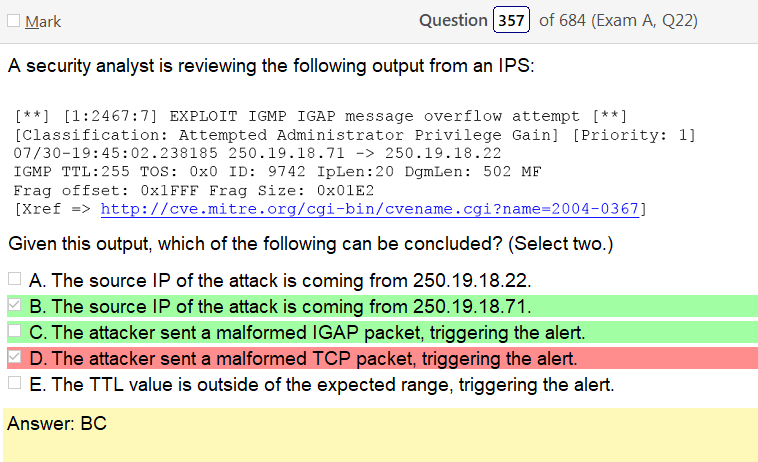
I’m not sure what an IGAP packet is or where its getting that. Its clear that its sending a packed and that there is an issue with it though. IGMP is an integral part of IP multicast. so I think its safe to assume its a multicast packet but the other part of this is IGAP packets are part of IGMP which is the indicator that its not a TCP.
Wow, I can actually figure out some of this stuff and maybe I’ll get a cert out of this. Awesome haha, only tie will tell.
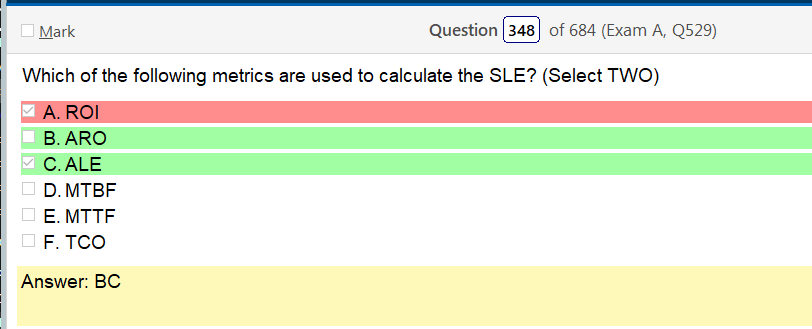
LOL, I totally forgot what these are and took a guess again. Humm, I just put on this show about people using computers and its some how more helpful in my level of focus than watching other shows haha
- ROI – Return on investment
- ARO – Annualized Rate of Occurrence
- ALE – Annualized loss expectancy
- MTBF – Mean time between failures
- MTTF – Mean time to failure
- TCO – Total cost of ownership
Single Loss Expectancy The Dollar Amount of what it would cost to replace the device if it malfunctioned or was lost, damaged or stolen. SLE x ARO = ALE ALE = Annual Loss Expectancy in dollars ARO = Annual Rate of Occurrence
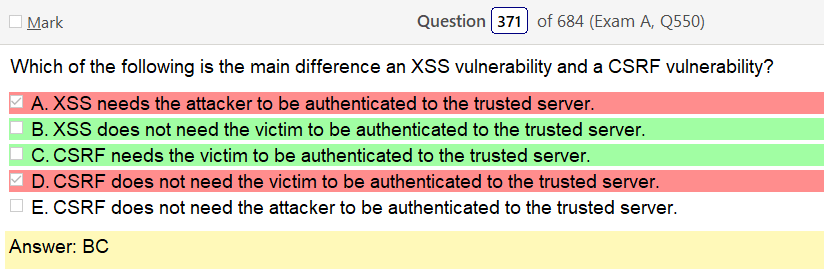
Clearly I got this one totally wrong. I’m not sure what CSRF is and apparently how XSS works. Personally, I think of it like pivoting which may be wrong. It seems like you have to be authenticated to something though dosent it? Or atleast connected.
Anyway, lets get a look at what CSFR is , also known as one-click attack or session riding and abbreviated as CSRF (sometimes pronounced sea-surf[1]) or XSRF, is a type of malicious exploit of a website where unauthorized commands are transmitted from a user that the web application trusts.[2] There are many ways in which a malicious website can transmit such commands; specially-crafted image tags, hidden forms, and JavaScript XMLHttpRequests, for example, can all work without the user’s interaction or even knowledge. Unlike cross-site scripting (XSS), which exploits the trust a user has for a particular site, CSRF exploits the trust that a site has in a user’s browser. So its basically the same thing but it does use a trusted connection. Honestly, that makes it cut and dry but I’m still confused about running java on a web app your not connected to? You know, this type of specific terminology gets really hazy, every time. There are specific ideas that people have behind it but as already noted in another question there isn’t much point to nailing down brass tacks on this if it works and its loosely within a idea. The crazy thing is that music genres work the same way.
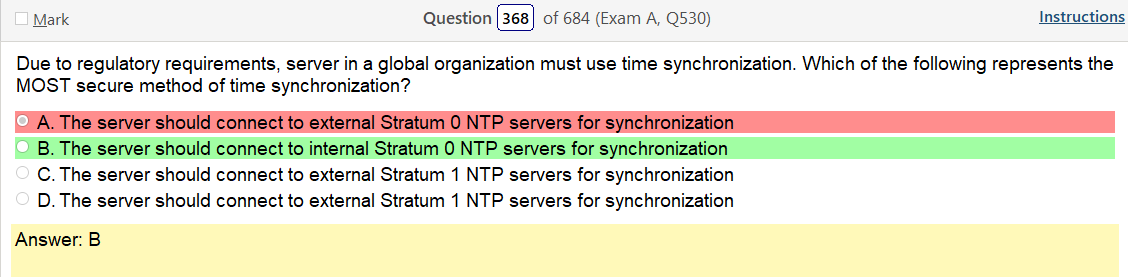
lol what the hell is this and why would use a single tier solution that’s completely internal. I can understand having a DC that replicates but having one internal point failure seems less than ideal.
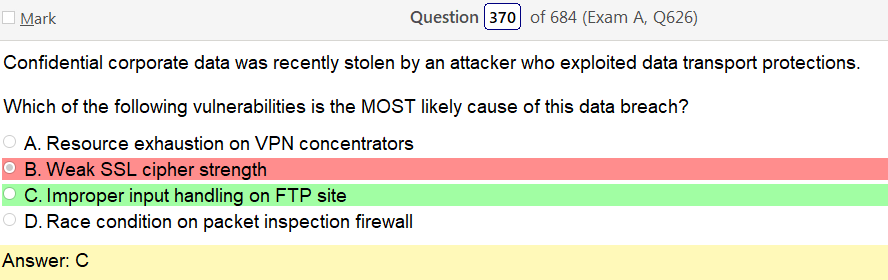
Input validation on an FTP site would amount to fuzzing which is not what they are talking about. It says transferring or transport protection. Not generic breaking and entering haha but ok though. I mean, your not fooling me with this FTP site shit its a storage server.
I think I got this wrong because I don’t know what IAM is so I guess I should figure out what that is Identity management, also known as identity and access management, is a framework of policies and technologies for ensuring that the proper people in an enterprise have the appropriate access to technology resources. IdM systems fall under the overarching umbrellas of IT security and Data Management.
There is no information about radius that I can find quickly so I’m just going with it.
I should have known this one but any way, here is a link on EAP-TLS certs
I actually looked this one up at the time and as previously noted MD5 is not great and AES was the correct answer.
This is so crazy, it selects a color and then mixes the two colors and that’s the key. Interesting, Diffie-Hellman key exchange
lol sick
This isn’t wrong but both of these are right given that there are thousands or hundreds of thousands of companies that manufacture IoT devices proving that they are all falling under one umbrella is kind of tough…
I’m not really sure why I put this here given that I got it right but there are a lot of factors and I feel its cut and dry.
This one seems opinion based changing the length would also be a good idea. That was my first answer.
All right, that’s all for now. I got a new phone yesterday and I might set it up before going to bed to let every thing sync. Who knows, wild adventure. I was waiting till a case I ordered came up but I’m not sure I really want to wait haha

Leave a comment