All right, spent a lot of time on some stuff last night and I’m still pretty sure that I still have a ways to go before really learning encryption, authentication and hashing. I haven’t made flash cards yet for this new fangled access control stuff (new to me haha). However, today’s a new day so lets get into these things again.
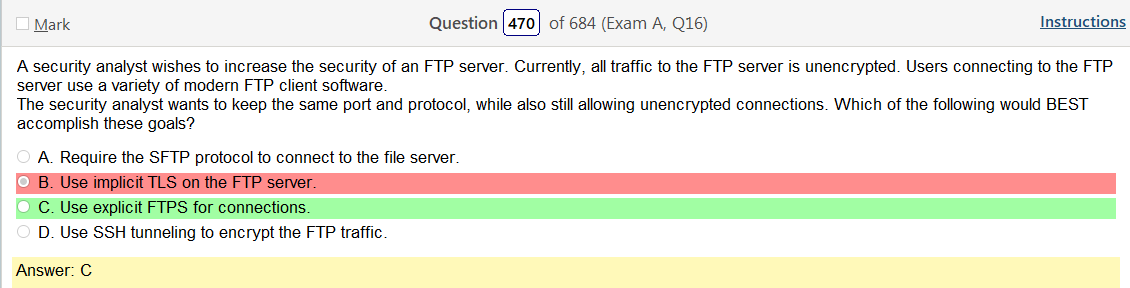
This one is confusing to me. Clearly TLS is encryption, as we figured out yesterday haha so that’s wrong but I was under the assumption that FTPS would use encryption so lets check that out
In explicit mode (also known as FTPES), an FTPS client must “explicitly request” security from an FTPS server and then step up to a mutually agreed encryption method. If a client does not request security, the FTPS server can either allow the client to continue in insecure mode or refuse the connection. The mechanism for negotiating authentication and security with FTP was added under RFC 2228, which included the new FTP command AUTH. While this RFC does not explicitly define any required security mechanisms, e.g. SSL or TLS, it does require the FTPS client to challenge the FTPS server with a mutually known mechanism. If the FTPS client challenges the FTPS server with an unknown security mechanism, the FTPS server will respond to the AUTH command with error code 504 (not supported). Clients may determine which mechanisms are supported by querying the FTPS server with the FEAT command, although servers are not necessarily required to be honest in disclosing what levels of security they support. Common methods of invoking FTPS security included AUTH TLS and AUTH SSL. The explicit method is defined in RFC 4217. In the later versions of the document, FTPS compliance required that clients always negotiate using the AUTH TLS method.
Lol so the term explicit means it asks if you want to encrypt traffic or not. Got it.
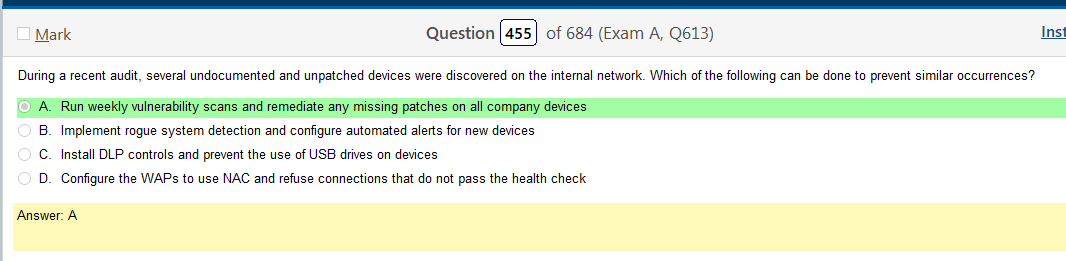
Honestly, I picked the right answer but I think what amounts to running red team exercises as preventative maintenance is not ideal. You should have computer accounts for every PC in your domain and use NAC. Rogue system detection is also a really good idea. The thing that some of these questions seem to imply is that your not using an AD environment, and I get that, but in most companies your not going to be able to authenticate to a WAP without an account. NAC with health checks also solve the issue of patching.
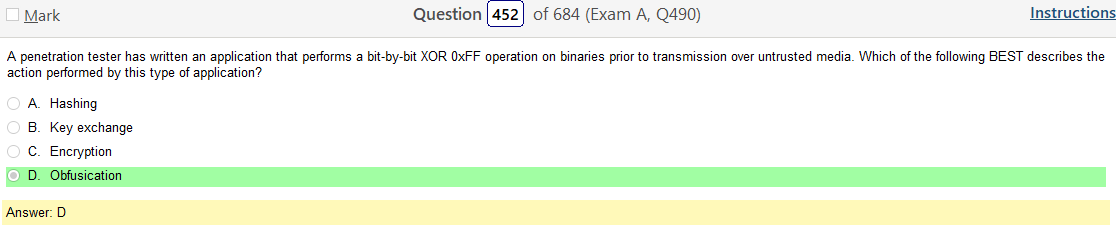
Pretty sure I know what obfuscation is but I wanted to go over that one again.
You know, I was hoping to put a simple definition here in italics but that isn’t working so here is a detailed account A question of security: What is obfuscation and how does it work?
Since we are here, lets go over XOR 0xFF, if we can
Nowhere to Hide: Three methods of XOR obfuscation
This is really good and somehow while doing this I’m reminded that I love doing this kind of work and that I’ve been doing it with art and music my entire life. I love research and learning that this points to this which points to this and somehow makes this work. Do you see that there? Looks like this over here, doesn’t it? It makes the world less random to me.
Anyway, it looks like this basically a method of encrypting code. I’m not a coder or anything close to that so I could be misinterpreting.
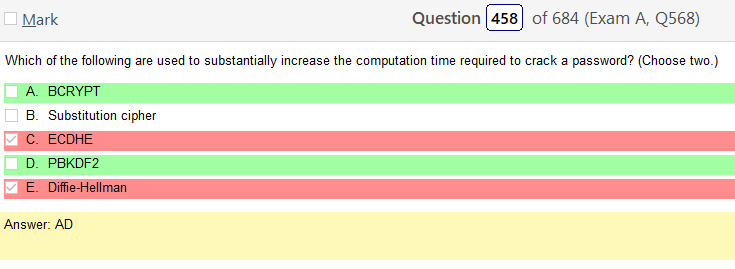
First off Diffie-Hellman has nothing to do with this, what so ever. Second, I’m not really sure what the other stuff is haha
- BCRYPT – Besides incorporating a salt to protect against rainbow table attacks, bcrypt is an adaptive function: over time, the iteration count can be increased to make it slower, so it remains resistant to brute-force search attacks even with increasing computation power.
- Substitution cipher – basically you shift letters, not a hashing method for passwords
- Elliptic-curve Diffie–Hellman (ECDHE) – key agreement protocol that allows two parties, each having an elliptic-curve public–private key pair, to establish a shared secret over an insecure channel.[1][2][3] This shared secret may be directly used as a key, or to derive another key. The key, or the derived key, can then be used to encrypt subsequent communications using a symmetric-key cipher. It is a variant of the Diffie–Hellman protocol using elliptic-curve cryptography. again, “diffie-hellman has nothing to do with this”
- PBKDF2 – In cryptography, PBKDF1 and PBKDF2 (Password-Based Key Derivation Function 2) are key derivation functions with a sliding computational cost, used to reduce vulnerabilities to brute force attacks.
Ok, hopefully I can remember these things because if you know what they are its obvious.
Shew, this isn’t as bad as, shit, this is authentication isn’t it? yep. ok. So, at first I was all “i’m not learning all this because I don’t really think I’ll need it but I’m realizing its better to take the time with it to actually learn it.
Not sure if this will really work to individually define these things with links but lets see what we can dig up.
- WPA+CCMP
- WPA2+CCMP
- WPA+TKIP
- WPA2+TKIP
lol, ok so I made a list and then found this which is super helpful and I’m saving it to my book marks bar as it answers a lot of questions and gets me going down the road to learning all these combinations.
WEP, WPA, WPA2, TKIP, AES, CCMP, EAP.
There is still a lot to learn and its 9 years old. However, its a solid start. You would think I would be further along with some of this stuff but I’m not.
Well, once again this proved to be more work that I thought it would be. Which might be why I was avoiding doing it and hoping that I would mysteriously know the answers without putting effort in. Unfortunately, that’s not real life.

Leave a comment