Still having some blogging to do. That last one was a a page turner haha. I mean, if your into learning this stuff. There are so many interesting sources of information on the internet that seen relevant and the issue with them is, how in the world am I supposed to consume all this. So, the goal is to find streams of information that seem accurate and relevant and I try to post links to that on here while keeping an eye on the encyclopedia of info that is free to use online. That’s the good and bad thing about the whole open source nature of CompTia exams. MicrosoftDocs is great but as you may have noticed they don’t have step by step tutorials with a lot of documented screen shots as vendors that integrate with their technology do. So anyway, lets get into study time and as previously noted, this is an exam study blog haha so feel free to click on stuff.
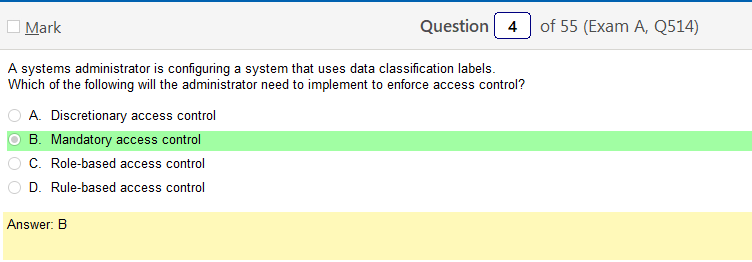
So these generic access control things kind of drive me nuts so while I understand MAC, I’m not quite clear on the others and wanted to back through that
Ok so before we get started I found this on Stackexchange and liked it: MAC makes decisions based upon labeling and then permissions. DAC makes decisions based upon permissions only. RBAC makes decisions based upon function/roles.
- DAC – all these are confusing but here goes: Discretionary Access Control Discretionary Access Control (DAC) was originally defined by the Trusted Computer System Evaluation Criteria (TCSEC) as “a means of restricting access to objects based on the identity of subjects and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission (perhaps indirectly) on to any other subject (unless restrained by mandatory access control)”. In practice the use of this terminology is not so clear-cut. In the strictest interpretation, each object controlled under a DAC must have an owner who controls the permissions that allow access to the object. Although many modern operating systems support the concept of an owner, this is not always implemented. In particular the standard does not cover “owners” leaving a problematic definition when group ownership occurs. also the objects in question have an ‘owner’ with read/write/permission control
- MAC – Mandatory Access Control: this one is role defined in that rather than the object having users associated with it, the information has a label and the users have assignments of what labels they have access to is system-enforced access control based on subject’s clearance and object’s labels. Subjects and objects have clearances and labels, respectively, such as confidential, secret, and top secret. A subject may access an object only if the subject’s clearance is equal to or greater than the object’s label. Subjects cannot share objects with other subjects who lack the proper clearance or “write down” objects to a lower classification level (such as from top secret to secret). MAC systems are usually focused on preserving the confidentiality of data.
- Role-based AC – You would think that MAC would have this name but it doesn’t. Any way, its pretty much the same thing but more granular
- Rule-based AC – RuBAC (i think that PBAC P is for policy, is the same thing) honestly, im not sure the internet thinks this one is real for data access but I did find this pertaining to networking: With rule-based access control, when a request is made for access to a network or network resource, the controlling device, e.g. firewall, checks properties of the request against a set of rules. A rule might be to block an IP address, or a range of IP addresses. A rule might be to allow access to an IP address but block that IP address from use of a specific port, for example port 21 commonly used for FTP, or port 23 commonly used for Telnet. A rule might be to block a specific IP address, or block all IP addresses from accessing certain applications on the network, such as email or video steaming.
Ok, I feel like I’ve sort of defined this but to be honest I may have to dig through it again. Anyway, one question in and I have a headache but lets look at the other ones related to this
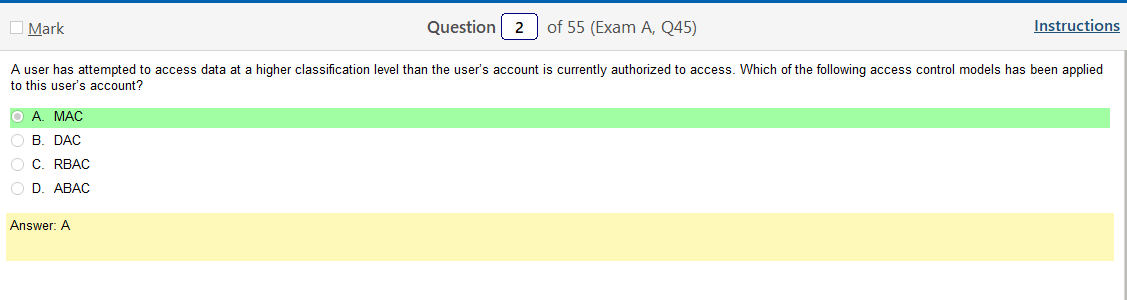
This one is cut and dry with the question of access control and using labels or classifications of data. That’s clearly MAC
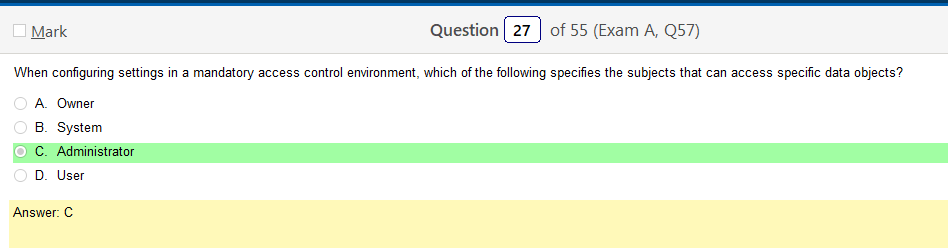
MAC has admins and DAC has owners of data. Not really sure about that for RBAC, guess I could check that out. Ok, looks like its the same as MAC in that there are admins and then users however it seems to very based on flavor as to what they are called. Other than admin.
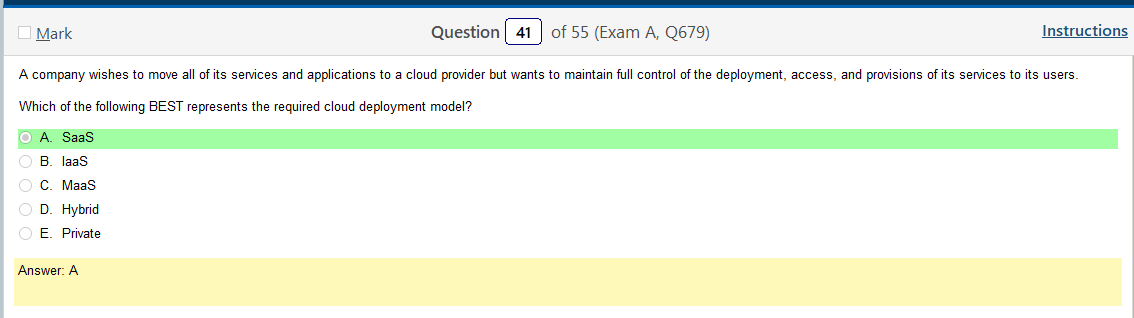
I feel like some of the classifications with these require clarification. There are probably more of these that I need to cover and I may get back to that at another time but for now lets look at these two slides
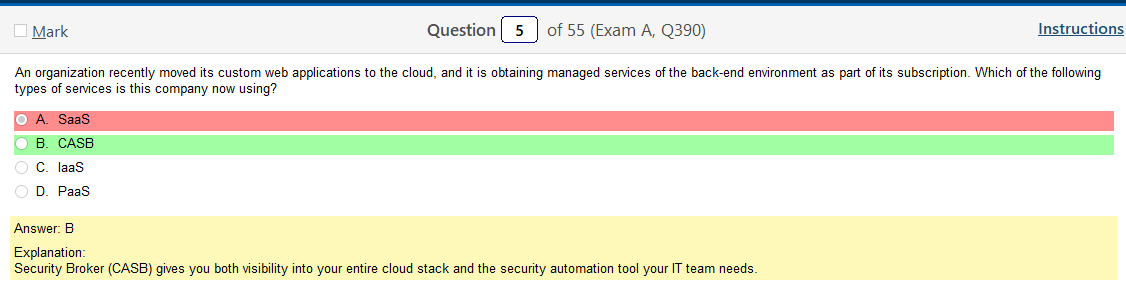
I don’t understand how managing back end services isn’t what the first one is saying. So, I think there are some issues here with wording as a What Is a Cloud Access Security Broker (CASB)? is a service that hardens your access to your cloud resources. There is also Security as a Service, in addition to Software as a Service. The first question makes sense and I think this second one is poorly worded as its not describing any thing having to do with security. I mean, managed services of the back end is what a CASB is talking about but its not exactly accurate.
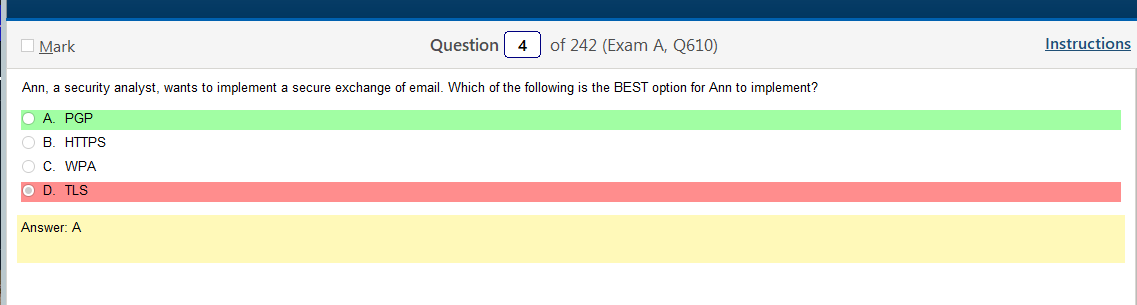
The thing is, I dont know why you wouldn’t use TLS but lets find out.
Per stackexchange: SSL/TLS protects the email from tampering or eavesdropping as it transits between your computer and Google’s server, and possibly during further relays to eventual recipient. And that’s all it does. PGP does far more. If you’re sending a signed email, the recipient can verify that the email was sent by you, and that it was not tampered with at any point between when you wrote it and when they received it. If you’re sending an encrypted email, you know that nobody but the intended recipient can read it — not Google, not the NSA, nobody. That’s why it’s called “End to End Encryption”. However, the email metadata (from, to, subject, time stamps) is still sent in clear, and PGP can’t help with that. So in general, it’s best to send PGP-encrypted emails via TLS-secured connections.
So that is some help. Anyway, that’s all for tonight. I feel like I learned a lot about my being better at my job but that is immaterial at this point as im only interested in one thing, getting through my shift haha

Leave a comment